

 IISRI® RATINGS AUTOMATED BY CYBERRANK
IISRI® RATINGS AUTOMATED BY CYBERRANK

CyberRank transforms the way we evaluate companies and their commitment to active cybersecurity.
IISRI® Ratings now powered by AI for Unmatched Success Now powered by AI, IISRI® Ratings combine years of cybersecurity and privacy expertise with cutting-edge automation. Get instant, powerful insights that make security and compliance simpler than ever.
CYBERRANK NOWThe best way to assess, manage and monitor your suppliers with the leader in Security and Privacy Assurance CYBERRANK NOW AND 60 CREDITS ON US TO SPEND IN
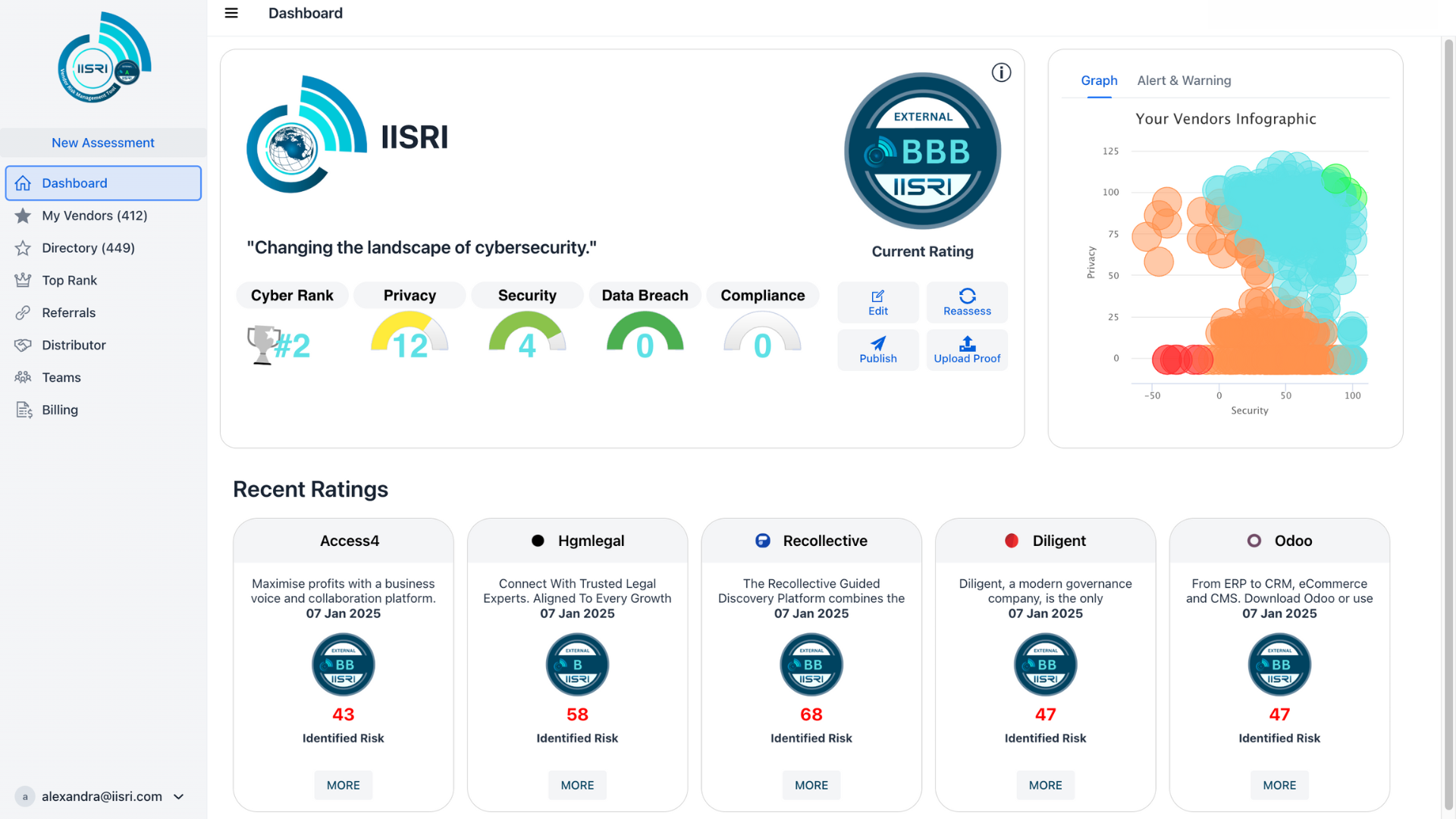
What is CyberRank?
CyberRank is the SaaS tool behind IISRI® Ratings, designed to streamline audits and Vendor Risk Management. Powered by AI, it helps organizations manage and reduce risks from third parties like vendors, suppliers, and service providers. With CyberRank, compliance with major security standards and regulations—such as ISO 27001, PCI, NIST, and EU DORA—is largely automated, saving you time and effort while keeping risks in check.
The most cost effective solution on the market.
Data leak detection
CyberRank is connected to all public data breach databases and continuously monitors for any breaches involving your vendors or exposed credentials.
Assets Discovery
CyberRank includes automated public asset discovery tools that help identify assets and extend our security and privacy testing. While the main public website is the primary focus, knowing and testing all assets allows us to have even a better indication of the security and privacy posture of the vendor.
Compliance
CyberRank helps you see how your organization and other companies measure up in key security areas, while also checking if vendors follow important standards like SOC 2, ISO 27001, HIPAA, and more. These certifications show they prioritize protecting your data and help reduce risks. You can also find out if any security breaches have occurred that might impact your organization. Want to boost your score? Upload private certifications or standards you meet to improve your CyberRank rating. Ratings update daily, so you’re always up to date.
Security Testing
CyberRank performs non-invasive security testing for known vulnerabilities on all publicly facing servers. Together with the given sector and location of the vendor, this will give a good indication of how likely a security breach is going to happen that could expose your data.
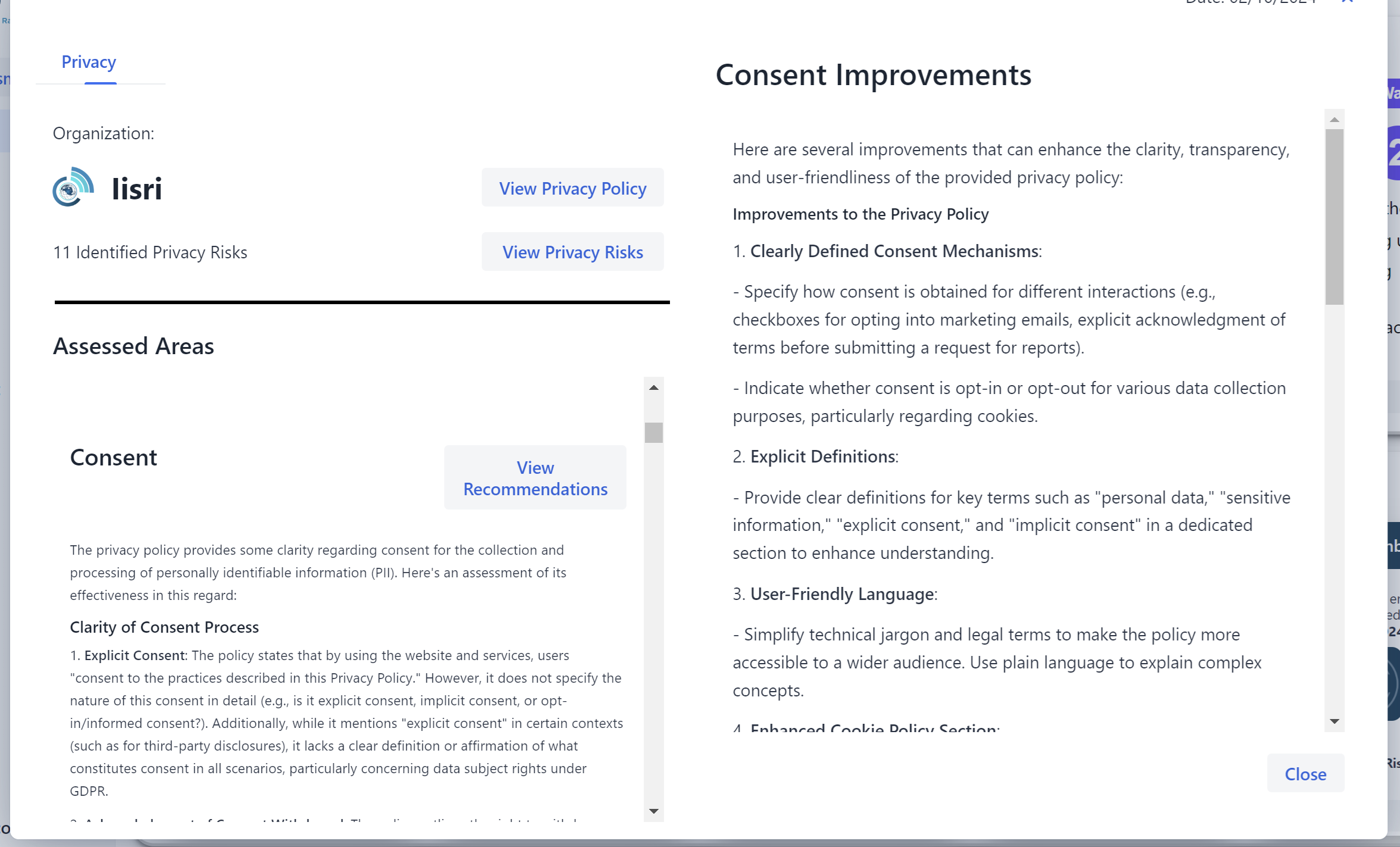
Privacy Testing
Our CyberRank tool CyberRank is equipped with advanced technology for analysing the privacy posture, including privacy policy and technical checks on deployed cookies and privacy consent banners.
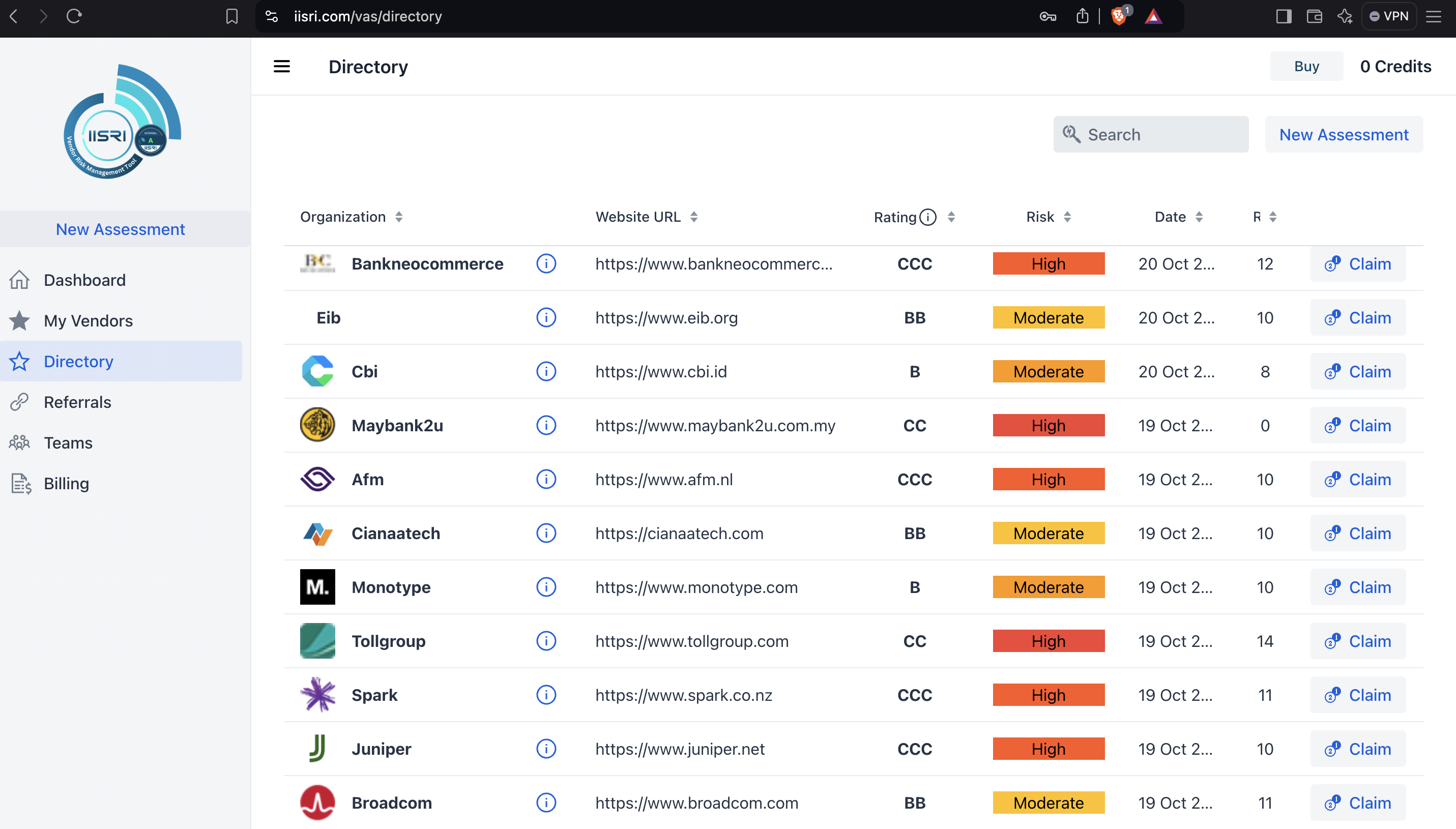
Vendors Access
All assessed vendors can access their ratings, review findings and recommendations. If they like to improve the rating they can also upload their certifications, assurance reports, and additional evidence, and request a re-evaluation.
Automation and Monitoring
As a customer, you just sit back and use our automated CyberRank. You can select the vendors you wish to continuously monitor and receive alerts and notifications if a vendor's rating is downgraded or if the CyberRank detects a data leak.
Pay as you go
Our pricing plans are flexible: an affordable credit-based system which enables you to target vendors as you please and pay only for what you use.
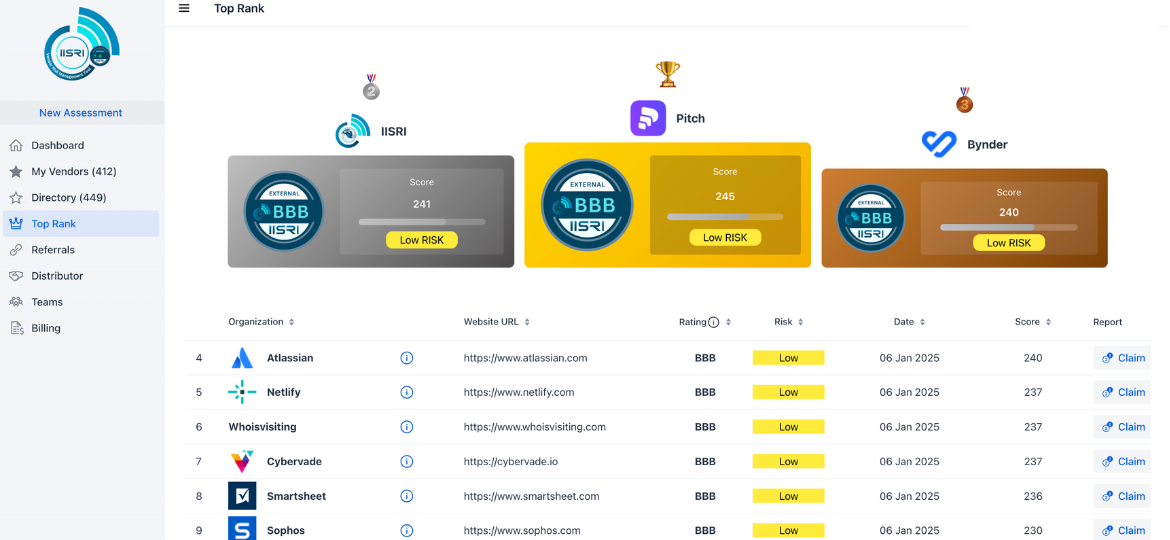
Get Instant recommendations how to imrove your companies CyberRank Rating
In just a few minutes, CyberRank provides instant, tailored recommendations to boost your rating. It’s the fastest and most effective cybersecurity consultation you’ll ever experience!
"Get Cyber Rated today with CyberRank by IISRI® and discover how you measure up in Cybersecurity and Data Privacy against the world’s best!"
CYBERRANK NOW!
I agree
